As usual, I was looking for subdomain takeovers. And I found a few so I reported them. For some I got a reply. But it seems like other companies just don’t care.
As the title says, one company referred to a vulnerability as low risk after reporting it to them. But more on that one later in the post.
Note that names of companies and people have been redacted in this post although I was considering naming them.
So first, let’s start with a subdomain takeover for a website that doesn’t need much security as they have no login form and do not handle any customer information. As I expected, no security contact information anywhere on the website. So I email the one address that I could find asking for a security email address.
No reply. I try again.
And I get a reply basically saying that the email was ignored as they thought it was spam.
As requested, I provided the information.
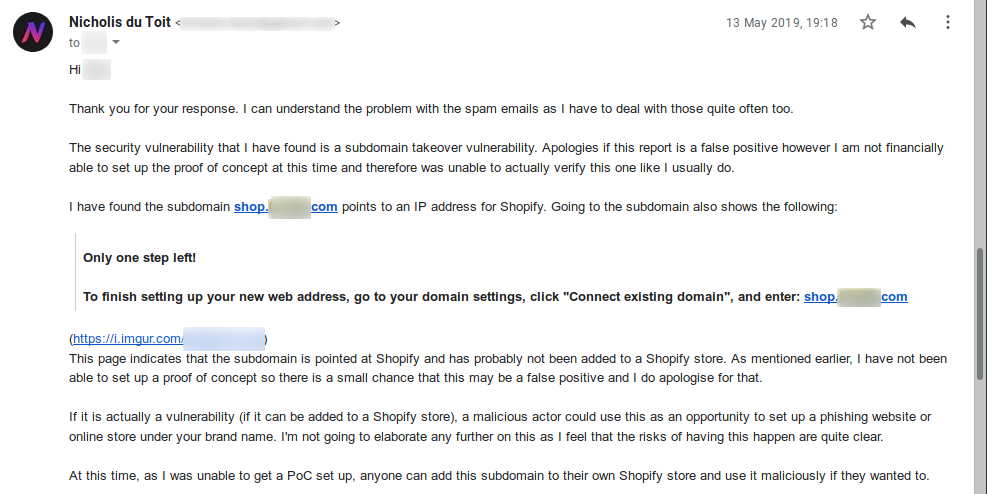
And no reply. So I follow up with another email.
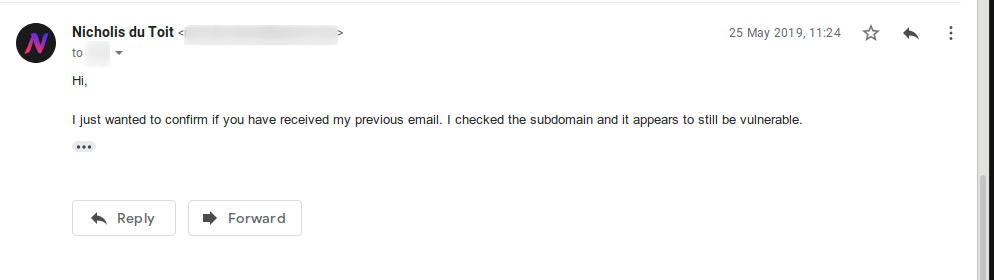
No further reply and at the time of writing, the subdomain is still up and could possibly be vulnerable to a subdomain takeover. To be honest, I was partially expecting that they wouldn’t care about it.
But would a bank care more about their security? The answer to that is no. I reported the security vulnerability to the only security contact I could find on their website.
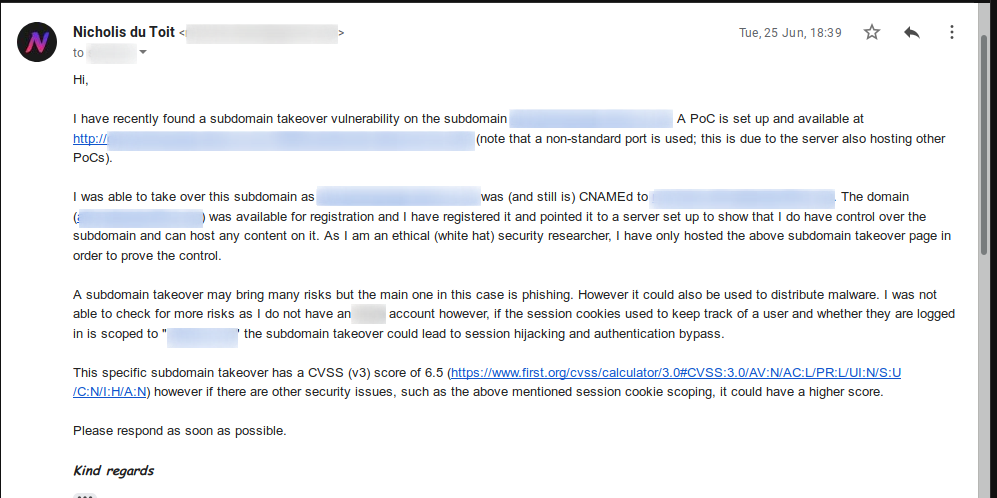
After that, I got an automated response saying that the security email is only to report phishing and that there is another contact for fraud. Basically, the bank cares only about phishing and fraud, not about any security vulnerabilites.
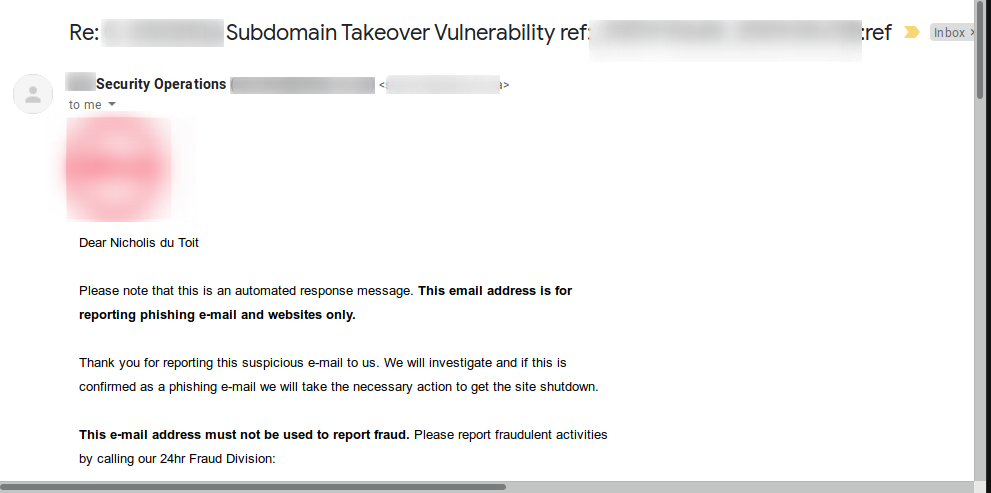
So I sent an email back.
So I contacted them on Twitter. Not sure how they don’t understand “security vulnerability” or “security issue” or how they confuse those with fraud.
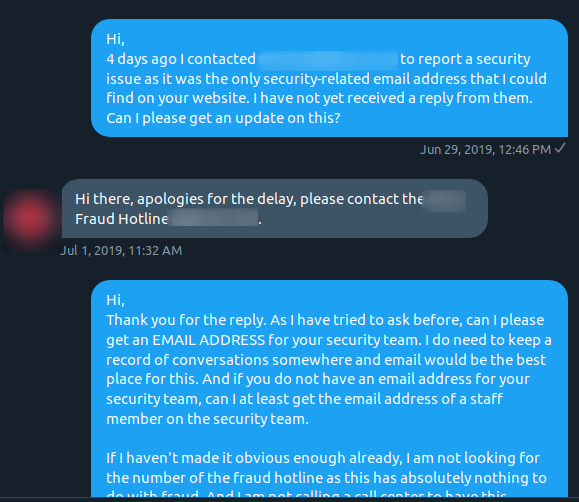
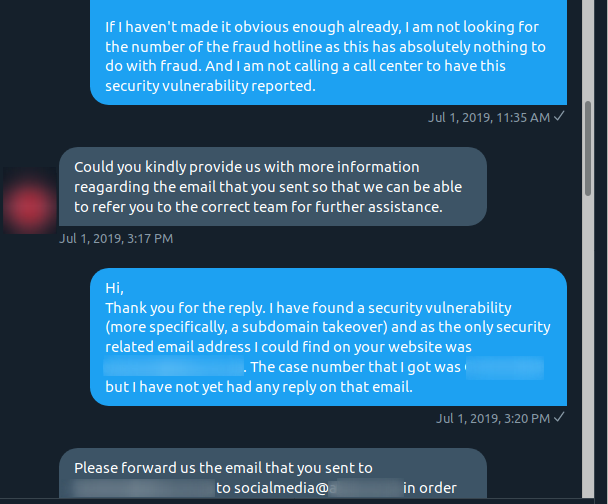
Yes, they did just ask me to forward emails containing full details about a security vulnerability to the entire social media team. Oh, and my phone number and ID NUMBER?! Why the f*** do they need my ID number? After refusing to do this, I was again told to contact the fraud hotline. I was quite annoyed before but at this point I was getting frustrated that a bank doesn’t care about security and can’t understand that I need to report a security vulnerability.
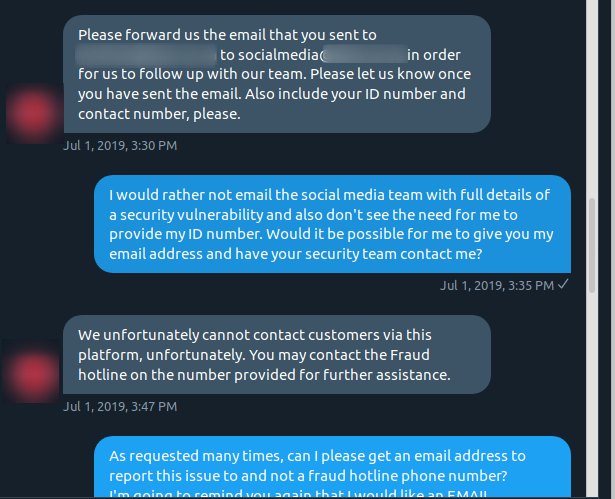
They then said that *they *provided the security email first. I of course told them where I found this email address.
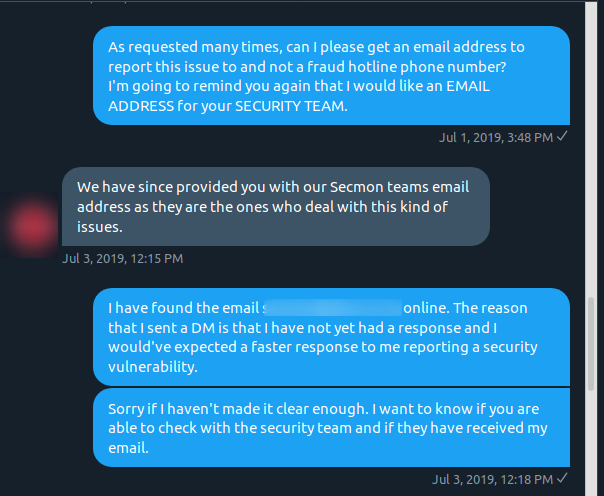
And they again asked for more information (which I have already provided). After this, and refusing to give me an email address, they provided me with the phone number of their head office even after I made it clear when first sending a message that I need an email address.
And later another follow-up email.
And, at the time of writing, the PoC is still online on one of the bank subdomains.
And, the one that you have been waiting for, the company that believes a subdomain takeover to be low risk.
I actually got a reply.
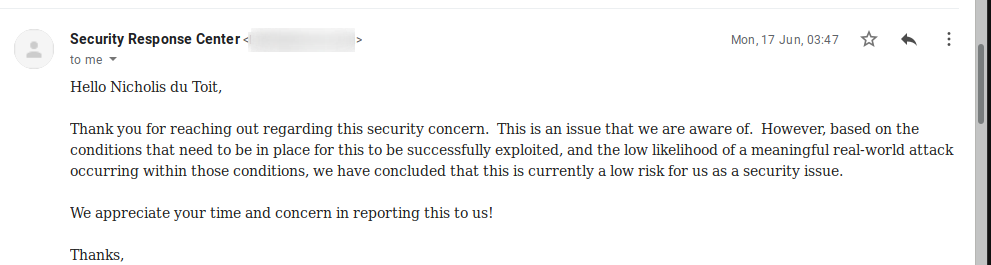
Wait what? They are aware of the issue. But then say “*based on the conditions that need to be in place for this to be successfully exploited, and the low likelihood of a meaningful real-world attack occurring within those conditions we” *consider it low risk. Someone didn’t read my email… I have successfully exploited the issue and created a demonstration of a real-world attack so I would consider it at least a medium severity issue.
So I ask them to reconsider.
And follow up a week later.
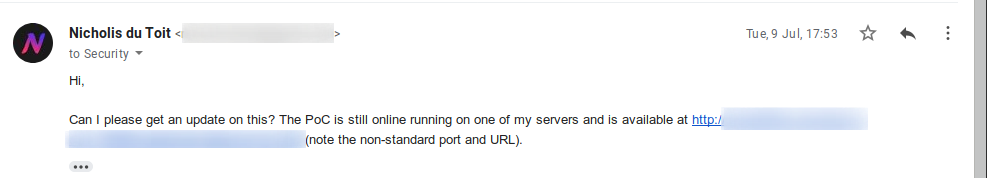
And I receive an email back from the stating that the PoC was down. This was the last email I received from them.
Around the time of the email, there was a BGP routing issue that may have affected their ability to access the PoC however I believe that the issue here was a different one. All PoCs on my server run on non-standard ports (not 80 and 443 but high ports such as 12345). I believe that they didn’t use the port number when checking the subdomain and this could’ve been a possible reason for them not being able to access the PoC.
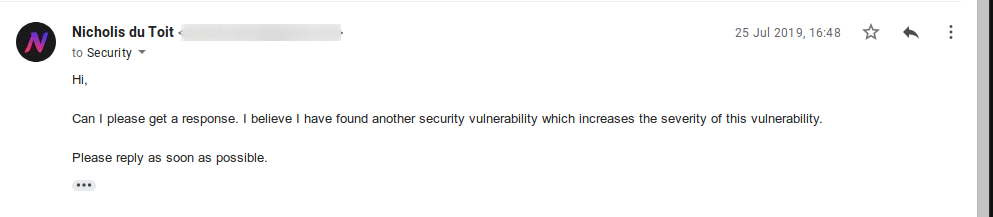
So I sent some follow-up emails to try to get a response. Nothing worked.
Then on 25 July 2019, I sent them another email after finding another security vulnerability that could increase the severity to high. I wanted them to reply first before I sent the details.
But that didn’t work. So I tried Twitter.
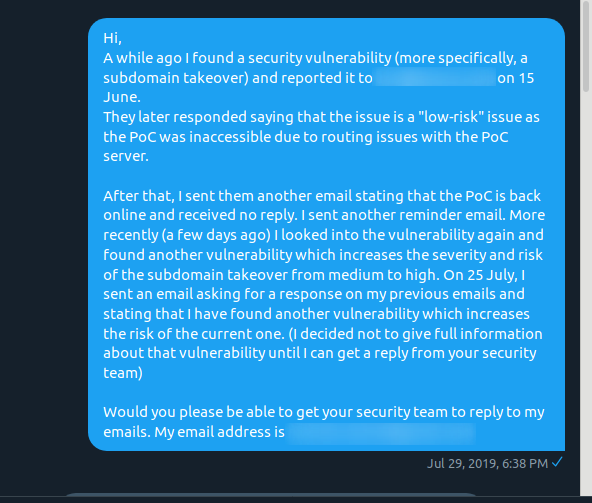
They really had to ask what department was handling my security vulnerability report.
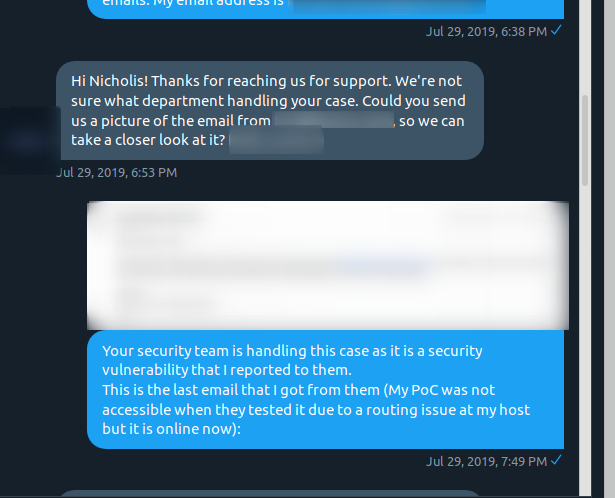
Somehow they forgot that I had a security vulnerability for their website, not one of their products.
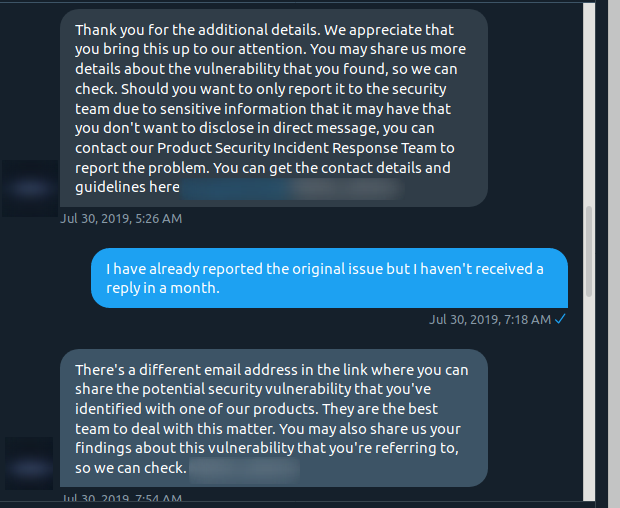
So I remind them that it’s a vulnerability in their website. And they sent me a link where I can provide feedback about their website. At this point, I’m not sure if the support agent can understand English.
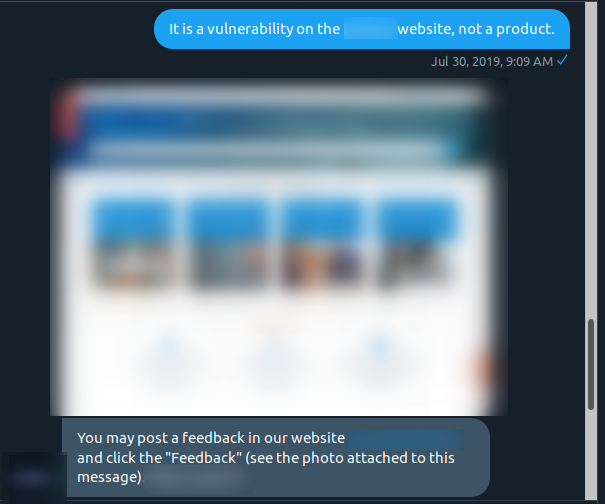
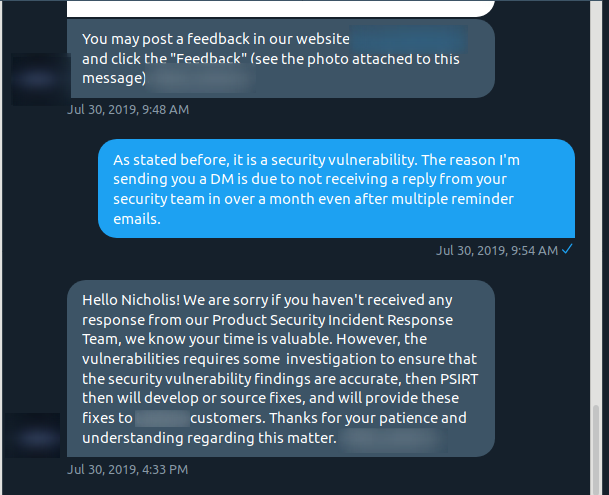
And after reminding them that it was a security vulnerability, they sent a message back saying that their Product Security Incident Response Team needs time to investigate so they can fix this and provide fixes to customers (basically implying security fixes for products, not websites).
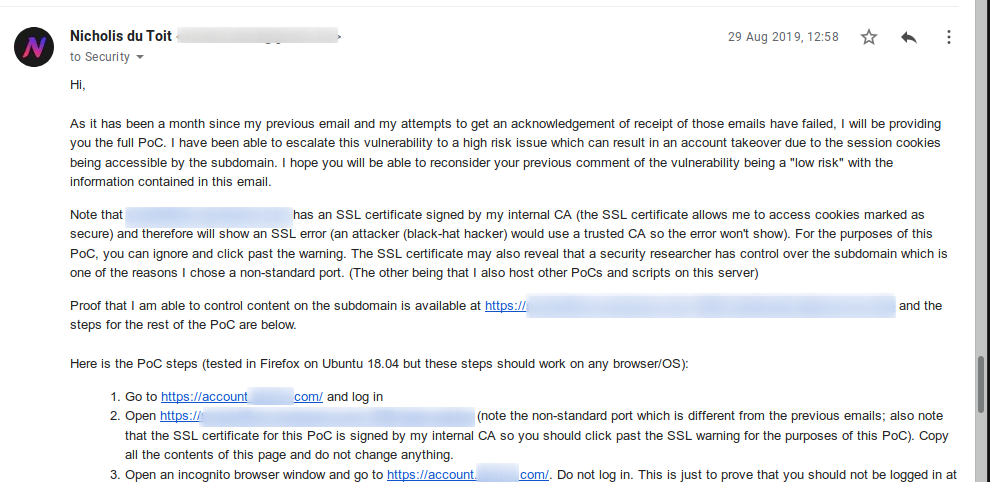
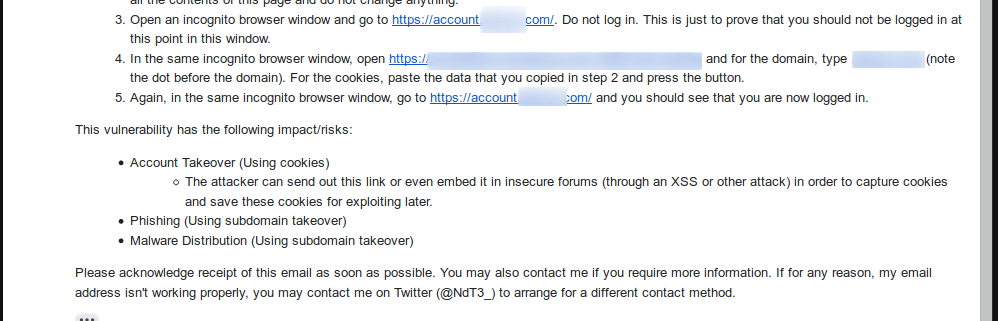
On 29 August 2019, more than a month later, I gave them the full PoC steps as I wasn’t going to wait any longer. It was obvious that they didn’t care. And yes, the PoC is still up.
So, in summary, some companies that really should care about security don’t. Maybe for some companies, money is more important than fixing a security vulnerability reported by a security researcher that is not well known.
Comments
Leave a comment
Please note that some comments may require moderation, as determined by Akismet. Read their privacy policy to learn more about how they process your data.